Hi’ya folks!
How are you all doing today?
Good morning!
My friends, come, it’s almost lunchtime over here. Me needs to cook something for myself soon. But before this, let’s begin our task for Day 11 of 100 Days of DevOps.
For context necessary, my brothers and sisters, I’m also doing this 100 Days of DevOps from Kode Kloud – so that it becomes part a web portfolio to show potential employers.
To help me find a job.
Okay.
Alright, let’s work together and let’s go.
We have the following task briefing from our smart folks at Kode Kloud.
The
Nautilusapplication development team recently finished the beta version of one of their Java-based applications, which they are planning to deploy on one of the app servers inStratos DC. After an internal team meeting, they have decided to use thetomcatapplication server. Based on the requirements mentioned below complete the task:a. Install
tomcatserver onApp Server 1.
b. Configure it to run on port8086.
c. There is aROOT.warfile onJump hostat location/tmp.Deploy it on this tomcat server and make sure the webpage works directly on base URL i.e
curl http://stapp01:8086

Okay.
First off, we must SSH into our web application server 01 (stapp01).
ssh tony@stapp01We enter our server’s password.
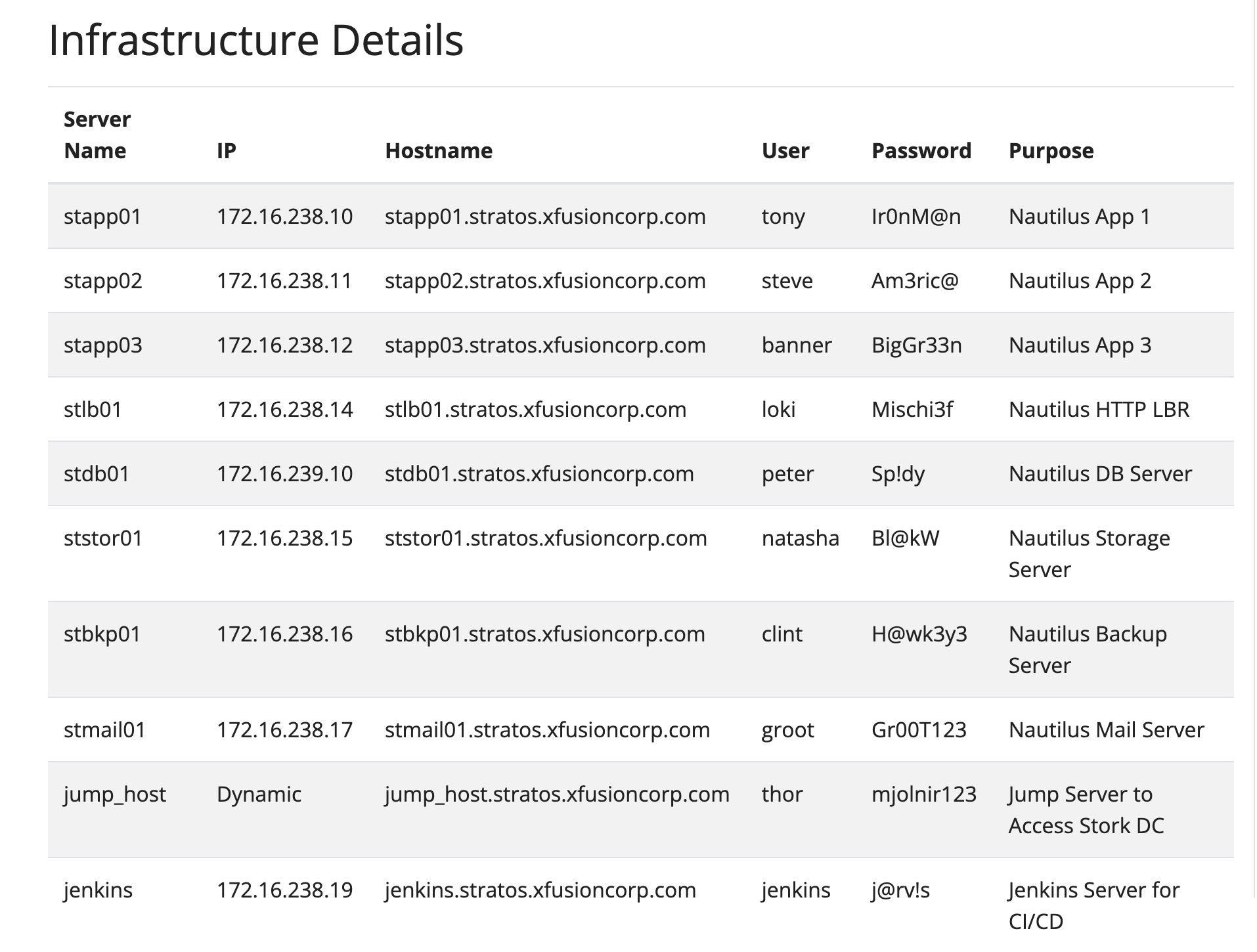
If you need to refer to details of Kode Kloud infrastructure relevant for this task. Friends, please go over this table:

Once we’re logged in to our web application server 01. We’ll need to install Tomcat server.
sudo dnf install sudo dnf install java-1.8.0-openjdk-devel tomcat -y tomcat -ySince we’re running on a 9th iteration, or version of CentOS. We’ll need to work with “dnf” for our package manager.
The Linux command above, invokes and asks “dnf” to find for us, and install two things.
- java-1.8.0-openjdk-devel
- Folks, I believe this is a Java SDK, a software dependency of Tomcat.
- tomcat
- Tomcat is also installed. As it is our web server for this task.
After dnf finishes installing. We’ll first need to configure our web server.
We do so, with editing a configuration file with an application called: “vi”.

We look for the HTML connector port (that has a default value of “8080”) and replace it with another numerical value “8086”. This changes the port of tomcat from 8080 to 8086.
Following instructions from our task briefing.
Press the key “i” to start making modifications. Find the connector port setting and change the port number to “8086”.

Finally, save changes and then exit the “vi” text-editor application.
Press “esc” followed with keys “wq!”.
Next, we’ll need to start the Tomcat web server service, and enable its auto-start process during boot up.
We do these through entering the following Linux command.
sudo systemctl start tomcat && sudo systemctl enable tomcatFriends, this is a compound Linux command. Meaning we’ve chained two commands going to “systemctl”. To start the Tomcat service. And then, for it to “enable” the Tomcat auto-start during boot process.

Then, optionally, you can check if Tomcat is already active and running. With this command.
Note: My friends, please remember that the “sudo” password for our web application server can be found over at our table above. Cheers!! 😀
sudo systemctl status tomcatThe print out for this command will tell you the present state, or status of our Tomcat web server service.
Next up.
We need to transfer a Java web application from the jump host. And move it to a system directory inside the web application server. Where Tomcat web server can begin serving it up for web access on HTTP port “8086”.
We call this process, deployment of an app.
Okay, folks.
First, we need to go back to jump host (currently, if you’re following along, we’re. logged in as “tony@stapp01”).
Enter the following Linux command. To move away from current SSH session and fall back to where we were from earlier (jumphost).
exitAlright.
Now, you should see “thor@jumphost” at the very first portion of your “shell prompt” – sorry, I don’t know what it’s called, really. If you see jumphost there, then we’re good to go.
We’re told that our Java web app is located inside our /tmp/ folder or directory.
You can do the following to quick check.
ls /tmp/This will print a list of the contents of the /tmp/ folder or directory.
Once we have this done. And if we see the web app called “ROOT.war” inside the /tmp/ folder (or directory).
We do what they call a “secure copy”. With this Linux command.
scp /tmp/ROOT.war tony@stapp01:/home/tony/Doing this will securely copy over the file “ROOT.war” from our jumphost to our web application server (at this directory /home/tony).
Folks, you’ll need to authenticate with the web application’s server password once more. And if you have proper authorization, the scp program will start copying the ROOT.war file into the web app server.
Then, we SSH once more into our web app server.
ssh tony@stapp01Enter your server password.
And once we’re in, you need to do the following.
sudo cp /home/tony/ROOT.war /var/lib/tomcat/webapps/Okay.
Let’s unpack the command above, and break it down into smaller pieces first.
- The “sudo cp” is necessary because we will be copying a file from our home directory to a system folder. Without “sudo” access, we can’t.
- /home/tony/ROOT.war – friends, this is the source directory and file path where the copying takes place.
- /var/lib/tomcat/webapps – and this is the system path where we need to “deploy” or copy our web app (ROOT.war) to. Folks, this is a folder where Tomcat expects files it needs to serve up (to make it available on a web browser, for example) to go to, and live.
And then, once this is done.
We do the following to check if we have the web app available on the web port “8086”.
curl http://stapp01:8086“Curl” is a Linux program that obtains information from things like website pages. That web servers like Tomcat makes available to other things like web browsers.
Alright, I think we have it up and running.
Okay, that’s that for now, folks.

Good job! 😀
Excellent, so far!
See you folks in our next lab exercise.
God bless. 🙌