Good morning, folks!
How are you guys doing over where you’re at?
Greetings from a small space.
Friends, today for our 5th Day of 100 Days of DevOps with Kode Kloud Engineer (if you want to check it out, or sign-up to learn with me, you can, for free, it’s at this link: https://engineer.kodekloud.com).
We’re given a task from the folks at Kode Kloud.
To install a security-focused set of tools for Linux.
It’s for making our Linux instances a little more safer for downstream activities geared for other people we serve, through our collective work.
Called, “SE Linux”.
Now, okay, let’s have a go at it. Shall we?
First off, we bring up Kode Kloud Engineer’s infrastructure. You can view it here (https://kodekloudhub.github.io/kodekloud-engineer/docs/projects/nautilus#infrastructure-details)

Then, we carefully read the briefing and instructions from Kode Kloud.
Our task is to…
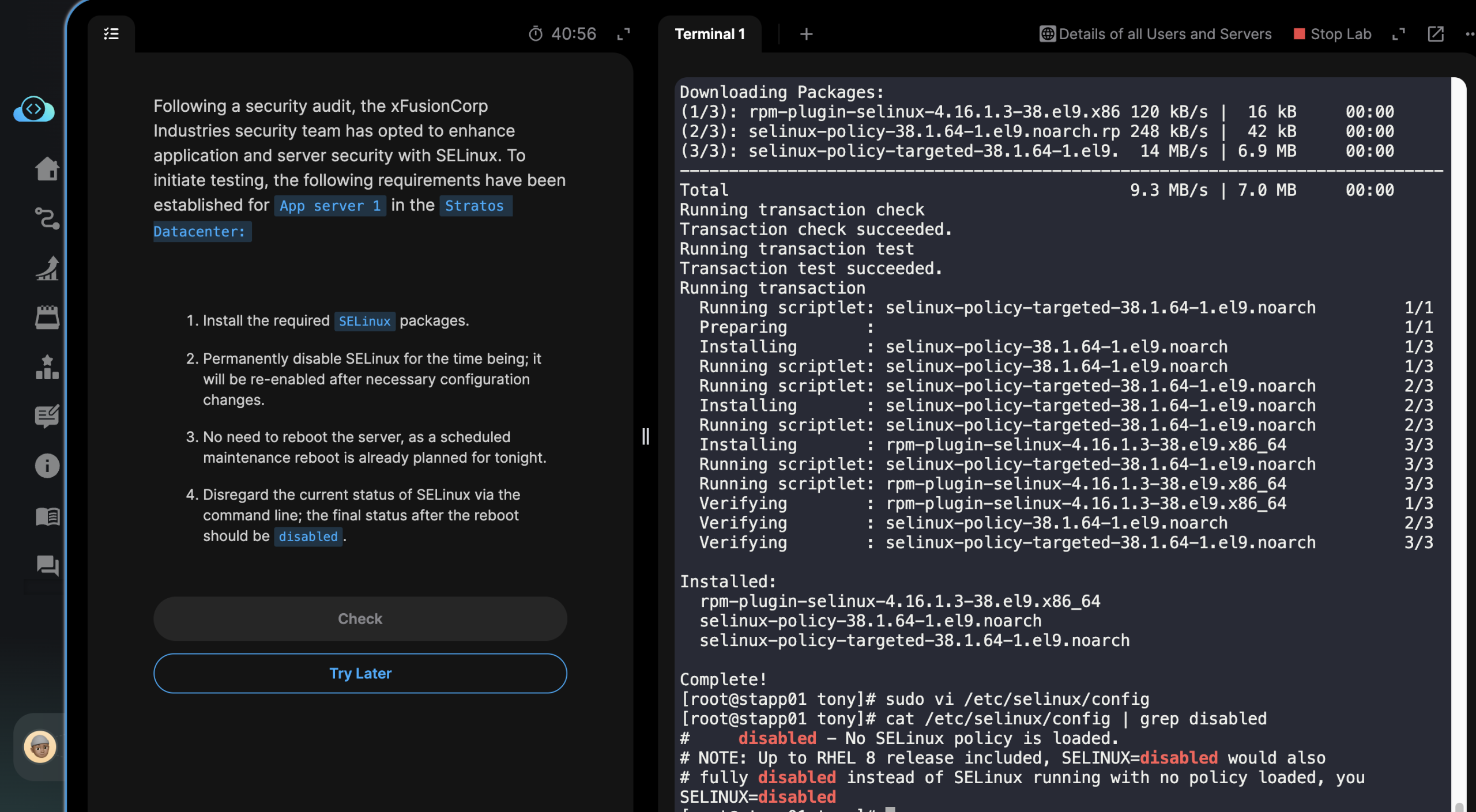
Following a security audit, the xFusionCorp Industries security team has opted to enhance application and server security with SELinux. To initiate testing, the following requirements have been established for
App server1 in theStratos Datacenter:
- Install the required
SELinuxpackages.- Permanently disable SELinux for the time being; it will be re-enabled after necessary configuration changes.
- No need to reboot the server, as a scheduled maintenance reboot is already planned for tonight.
- Disregard the current status of SELinux via the command line; the final status after the reboot should be
disabled.
Okay.
We have our task.

First off, we ssh into the needed application server. In this case, stapp01.
ssh tony@stapp01Once more my friends, you can ssh through the application server’s IP address. If the hostname doesn’t map properly to it.
ssh tony@172.16.238.10Then, enter the server application’s password for SSH.
You can find it listed on the table from Kode Kloud Engineer’s infrastructure schematics above.
sudo su -You might also want to elevate privileges to becoming a root user, temporarly.
Not doing this, might prevent you from doing this task properly. Or, you’ll see errors.
Folks, the root password is the same as your initial password for SSH for tony@stapp01.
sudo yum update -yInitiate to update the yum package manager.
sudo yum install selinux-policy selinux-policy-targeted -yThis begins to install SE Linux along with other necessary dependencies.
sudo vi /etc/selinux/config
Remember that we need to change the value from the SE Linux config file saying “SELINUX=enforcing”.
To “SELINUX=disabled”.
Without doing this, we will not be able to go forward with the task checker.
While running “vi”, press “i” to start making changes to the text file. With vi, pressing the key “i” invokes the program to insert mode. This allows you to tangibly make changes.
To save and exit your changes from the “vi” text editor. You need to press “esc” and then type “wq!”.
What does this do?
- When you press “esc” while editing a text file from vi.
- It will allow you to enter commands. Like to exit without saving. Or to save any changes made first, then exit the text file.
- In this case, we want to save the changes, and then, exit the file.
- So, what we can do is press “esc” first. Then enter the keys “wq!”
- “w” means to write changes to storage.
- “q” means to quit the vi text editor program after making the save.
- and finally, “!” means to force doing the preceding actions. Which, is to save first and then exit the application.
- So, what we can do is press “esc” first. Then enter the keys “wq!”

Optionally, you can invoke the “grep” command to look for the words “disabled” from the saved config file for SE Linux.
This will help you ascertain if the file had been tangibly changed. And that the changes were saved prior to exiting the vi text editor application.
Alternatively, you can also invoke this command to determine what is the status of SE Linux from your instance (in this case, we’re running on a CentOS 9 instance).
sudo sestatus
If your “sudo sestatus” returns a value of “disabled”.
You’re good to go.
Click the “check your work” button. To invoke Kode Kloud’s task correctness checker tool.
If you’ve done the task correctly, it should let you pass. Otherwise, it will show task failure. And then, you can choose to re-do this task.
Alright.
That’s it for now, my friends.
God bless you! And, thanks.
Leave a Reply