Peace be with you, my friends.
How are you folks doing?
In the holy Name of Christ our Lord Jesus, peace be with you.
Good morning!
Greetings from a small space, off the east-side of the pearl of the orient, the good islands of the Philippines.
Alright, today our task from Kode Kloud engineer learning program is this one.
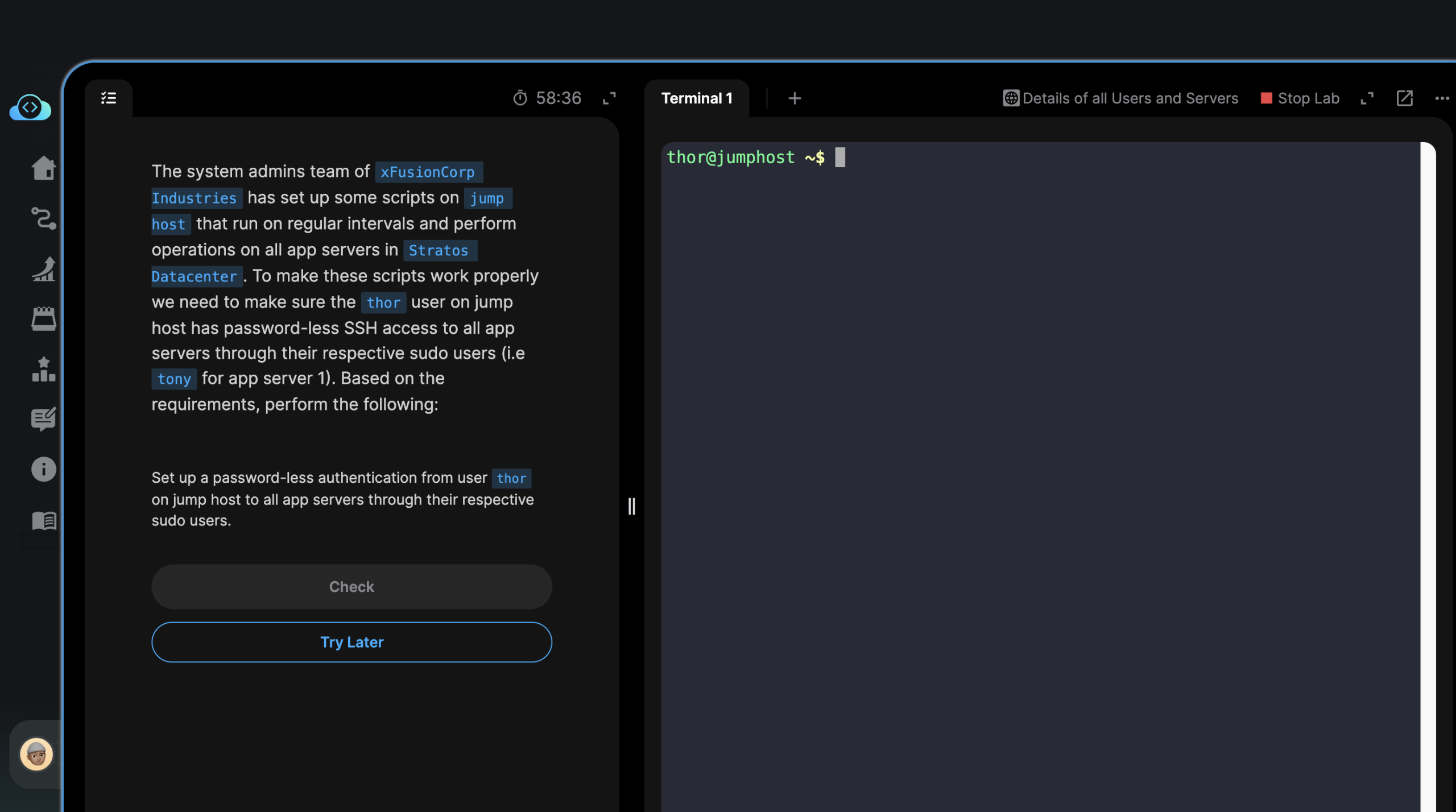
The system admins team of
xFusionCorp Industrieshas set up some scripts onjump hostthat run on regular intervals and perform operations on all app servers inStratos Datacenter. To make these scripts work properly we need to make sure thethoruser on jump host has password-less SSH access to all app servers through their respective sudo users (i.etonyfor app server 1). Based on the requirements, perform the following:Set up a password-less authentication from user
thoron jump host to all app servers through their respective sudo users.

Folks, we’ve been given a task to set-up a password-less connectivity (in terms of authentication and receiving authorization to do tasks) via SSH connection from our jumphost, to our application servers.
This means, we need to generate cryptographic keys (or also known as SSH keys) from our jumphost (origin, with user “thor”) to our application servers’ sudo users. Namely, these are the following.
- stapp01 (with user, “tony”)
- stapp02 (with user, “steve”)
- stapp03 (with user, “banner”)
Here’s the infrastructure schematics for our learning program at Kode Kloud engineer.


Once we have generated our keys with this command.
ssh-keygenWe securely copy our public key to each application server.
With these Linux commands. One for each server.
ssh-copy-id tony@stapp01ssh-copy-id steve@stapp02ssh-copy-id banner@stapp03And to verify that we have password-less access from our “thor” user on our “jumphost”.
We need to SSH from “thor@jumphost” into each of the application servers. Without having or needing to input their passwords anymore.
ssh tony@stapp01Like this one, and so on for the other two (2) application servers. Namely, “steve@stapp02” and “banner@stapp03”.
Once we’re able to log-in and connect via SSH without the server’s password.
If you need to check the servers’ passwords and other details. Refer to the infrastructure schematics above.
Our task is done for today.

Alright!
Okay, it’s story time. Let’s talk more about this thing called SSH and keys.
SSH stands for “secure shell”.
It is technology that allows someone outside of a network of servers. To securely connect to a server at that network.
Folks, I believe everyone of us do this. Often, without our knowledge.
When you generate keys for SSH. You generate what’s called an “cryptographically asymmetric keys”.
Meaning, a software program creates two keys, or a key pair.
One is called a public key.
The next one, the private key.
And both are necessary, and play an important role to security.
I’m no longer going to delve into details about these. However, it is good to note that if the other key encrypts information or data. Only the other key can decrypt, or unlock it properly.
If you want to learn more about asymmetric keys.
I believe this YouTube explainer video will be helpful.
https://youtu.be/_zyKvPvh808?si=wCOxWF2EGYBnMV7b
Asymmetric key pairs are very important to modern computing security. At keeping your online accounts, and whatnot secure. It is also at work with the website pages we visit. Like this page.
SSL or the connection that makes webpages communicate with other webpages securely online runs on a combination of symmetric and asymmetric key encryptions.
For example, through a secure internet connection called SSL. You can securely browse the web. It helps keep what you enter in form fields, like your name, email address, and postal address safe. And it prevents other unauthorized persons from reading or snooping on your website activities.
My friends, SSL is very good. It helps keep us all safe online. From cyber-criminals, from unethical hackers, and from scammers.
However, it is not fullproof. I believe nothing is. However still, having SSL or encryption enabled in your web browser session is best practice for anybody.
Your browser should warn you. If for example, you’re visiting a website that doesn’t have SSL. It could be potentially dangerous for you, or anybody, without encryption or security of SSL. Especially if you’re buying things online from a website or an online shop that doesn’t have it enabled correctly.
I don’t consider myself an absolute expert in the field of cryptography or security. However, it is part of my job to know a little. So that working together, we can keep other people we serve safer online. Through our products and services we make available to you.
Anyway, enough about this for now, my friends.
What happens in our task. When we generate a key pair from our jumphost (under a user called “thor”).
One public key.
And second, a private key.
Then, we securely copy our public key to all the other application servers.
Doing this, allows us to securely login or SSH from thor@jumphost into the application servers we’ve copied our public key to. Like app server: “banner@stapp03”.
Remember, that thor@jumphost still retains a private key.
Once we attempt to SSH or log-in to an app server with our public key. The app server checks for the private key.
If it sees the right private key. It lets the SSH connection establish.
This way, we don’t need to write and input a password every time.

That’s it for now, my friends.
And, may the good Lord of heaven and earth be with you all, my dear brothers and sisters in Christ.
May God bless us.
Kapayapaan nawa’y suma-inyo at suma-ating lahat.
Salamat po.
Leave a Reply